Much of us have had no choice but to be at home teleworking, some to do good and others to enter the dark side. In this article we will talk about some vulnerabilities that have been found in the most used tools during confinement.
Vulnerability in Zoom
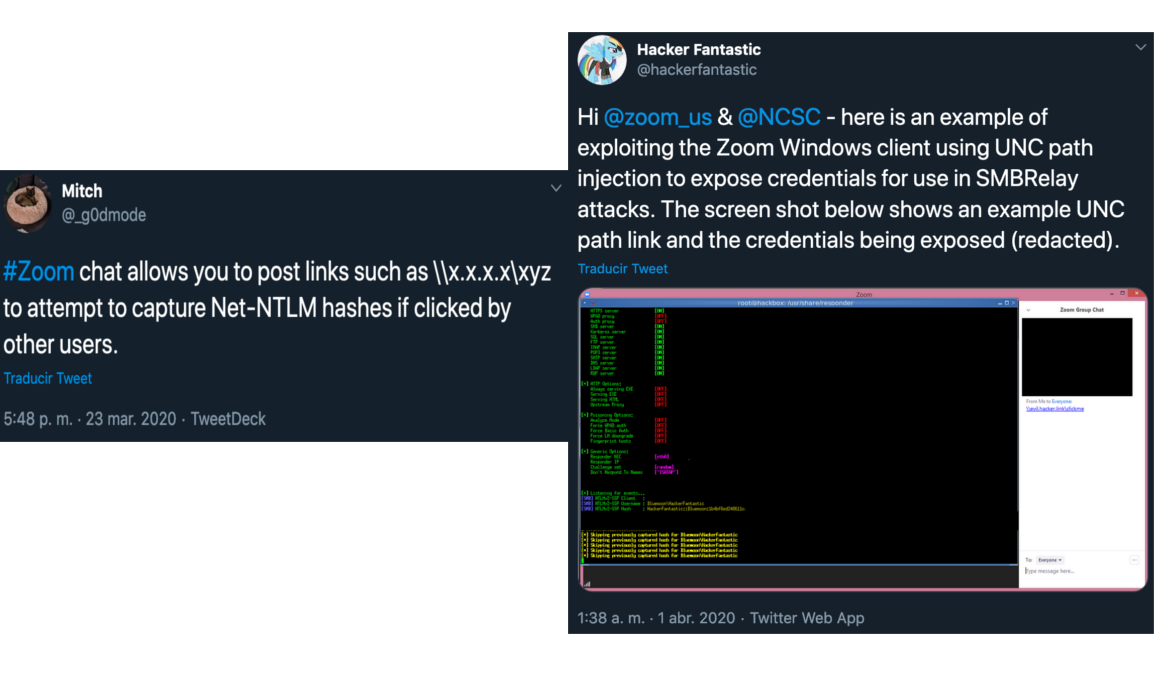
Zoom is an application of videoconferences and virtual meetings for Windows, Android and Apple platforms for both PC and mobile devices. It all started with the discovery of a BUG , found by the expert in computer security @_g0dMode , with pseudonym Mitch , and published on their Twitter account " ZOOM allows you to publish links such as \\ XXXX \ XYZ to try to capture hash net -ntlm values if other users click on them " on 03/23/2020.
Later, on April 1, Matthew Hickey, co -founder and technical development manager and the correct operation in House Ltd , performed the test and was effectively correct, the Bug came true. Matthew said in his tweet , mentioning @zoom_us and @ncSc , the following: " Next, an example of how the Windows zoom customer explodes, by injection of the UNC route, exposing the credentials, using Smbrelay attacks ... ". Matthew told Bleepingcompter , that in addition to stealing the credentials, programs could be executed when clicks in the link. To all this, Zoom Video made no statement or published in his blog nothing of what happened.
UNC or Universal Name Convention: Microsoft Windows defined UNC links to create a common syntax of how to specify the resource route .
We explain the process a little better:
Zoom for Windows uses UNC's to expose a link called hyperlink, when a user clicks on this link , the operating system works to establish a connection, to be able to access the resource without problems (whether it is a Word document, Excel ... or any other resource), it is here, when send your name and the hash of the NTLM fixed alphanumeric characters). This hash was intervened by cybercriminals and with deciphered methods could get your name and password.
On March 31, Bleepingcomputer gives us a provisional solution that helps this process not occur, modifying group security policies.
Zoom Video was working on the problem solving and with the update of the tools in version 4.6.19253.0401, he managed to make the UNC's links become hyperlinks.
WhatsApp releases 6 vulnerabilities in the security of its application
Computer security is not 100% reliable , and proof of this is the par excellence WhatsApp Messenger or simply WhatsApp.
Surely most of you have used the application to communicate with your coworkers or with your relatives. Well, be careful, because WhatsApp has noticed 6 striking failures in its famous application.
Bugs have been published on their new website dedicated to informing common vulnerabilities and exhibitions, standard nomenclature.
Two of the errors have been found through the rewards program and the other four, by code review . Let's start explaining them:
CVE 2020-1894: The problem lies in an memory overflow that allowed to execute code remotely through a message with malicious code . All those who have the Android version before V2.20.35 or Business V2.20.20 must update as soon as possible. Also included those who have an iPhone with the WhatsApp version prior to V2.20.30 and Business V2.20.30.
CVE-2020-1891: The user controlled a parameter of a video call, and allowed a writing outside the limits on 32bit devices. The Android devices prior to version V2.20.17 and Business prior to V2.20.7 and the iPhone devices prior to version V2.20.20 and Business prior to V2.20.20.20
CVE-2020-1890: An attacker could send an altered multimedia message , for example, the sending of a sticker, where he stores an intentional URL. Those who have an Android with the WhatsApp version V2.20.11 or the Business prior to V2.20.2.
CVE-2020-1889: The objective is the omission of security functions allowed by the exhaust of the test area in Electron, and the privilege escalation that is combined with any vulnerability of execution of remote code within the rendering process of the test area, allowed undue access in WhatsApp Desktop in the previous version to V0.3.4932.
CVE-2020-1886: In an buffer overflow, you could allow writing outside the limits through a video call , especially after receiving and answering it . Anyone who has the WhatsApp version on Android with version V2.20.11 or previous and the Business prior to version V2.20.2.
CVE-2019-11928 : In the WhatsApp Desktop, in versions prior to V0.3.4932, an error in the entry validation could run a script within a location message .
Always having our updated applications is one of the tips that Gowtech remarks in its articles, to extend the life of our computer .
Microsoft releases new patches for all versions of Windows 10, which corrects vulnerabilities in Intel chips
Microsoft prepares for the great update for next year by liberation for patches for our favorite operating system.
And, in May of this year the version 20H1 was available in Windows Update, where improvements, failure remedies are found, but also many vulnerabilities. We refer to the latest Windows 10 version 2004 update, which fixes the problem of the universal Windows platform, Microsoft Store, which allowed the authentication of the login unique.
This is one of the 128 arrangements that have made in this last May update, but in September it has been released and is only available for those computers that have an Intel chip. It is associated with the KB457758 patch
The following list corresponds to the numbering of the patch associated with each version of Windows:
- KB4558130 for Windows 10 2004.
- KB4497165 for Windows 10 1909 or 1903.
- KB4494174 for version 1809.
- KB4494451 for version 1803.
- KB4494452 for version 1709.
- KB4494453 for version 1703.
- KB4494175 for version 1607.
- KB4494454 for other versions of Windows 10.
Remember that Windows 10 updates and the user does not have to intervene at all, except time to turn off or restart, so that the updates have effect.
The Gowtech team provides its services both to large companies and small users who need advice, commissioning of computer security or any other proposal related to the digital transformation of their business. Consult us .